A zero-knowledge password manager that keeps your passwords private by design.
Understanding the lifecycle of your data is key to trusting the system.
Your vault is created locally on your device. A random salt is generated.
Your master password is processed through Argon2id in your browser to derive the encryption key.
Your data is encrypted using AES-256-GCM. The key never leaves the ephemeral memory state.
The encrypted file is saved to your local storage. Passary has zero knowledge of its contents.
Every feature designed with zero-knowledge architecture in mind
Your encrypted vault never leaves your device. No cloud, no servers, no sync. Complete custody.
Argon2id + AES-256-GCM. The same cryptography protecting classified government data.
We never see your password or data. Even if we wanted to, we mathematically cannot.
Security is about trade-offs. We chose isolation over convenience.
Passary is spiritually similar to KeePass but built for the modern web. We use standard web crypto (Argon2id) and provide a polished, zero-setup UI that works in any modern browser without installation, while maintaining the same "local file" philosophy.
We believe in honest security. No product protects against everything. Here is our threat model.
Need a password manager that doesn't hide the details behind "easy to use" features? Passary is transparent about every aspect of its security and gives you complete control over your data.
If you don't want your passwords living in a big central database, Passary gives you complete custody. Nobody can access your encrypted vault except you. No "just trust us."
No sign-up. No app, no reset email. A traceless password manager with a dead simple model: one file, one password, your device, your data.
Complete visibility into encryption methods and protection mechanisms.
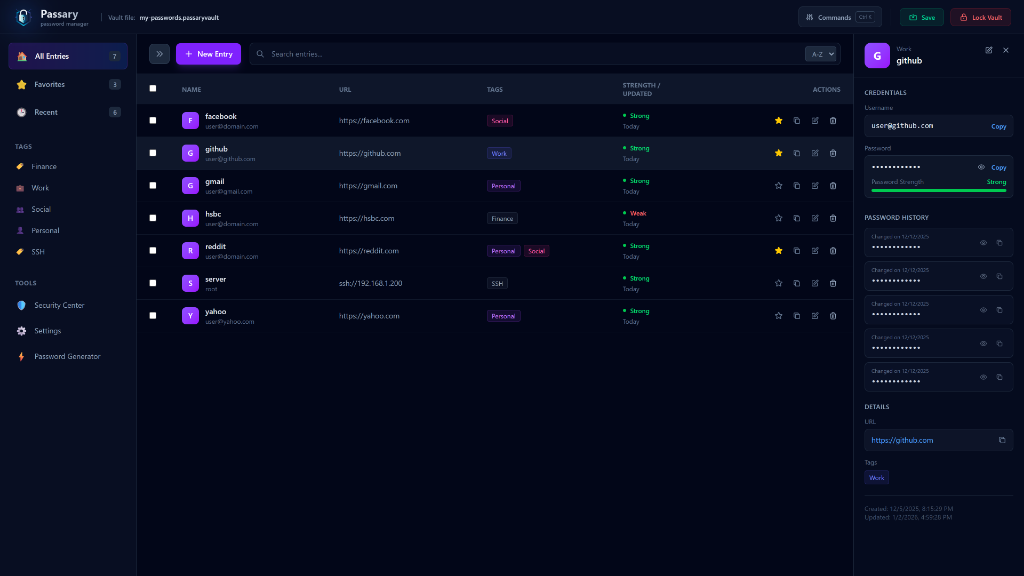
Analyze your passwords for strength, reuse, and weak credentials. Generate strong passwords.
Organize logins by folders, favorites, tags. Quickly filter and search by flexible labeling and smart views.
Quick search, keyboard shortcuts, and a minimal design so you can find what you need and get back to work.
Export your encrypted vault file at any time. Easily import from KeePass. Keep backups on multiple devices.
A clean, dark interface that feels like a developer tool. No clutter, just your passwords.
We are building for a specific type of user. If you fall into these categories, we might not be the best fit.
If you need your passwords to magically appear on all devices instantly without effort, Passary is not for you. We prioritize isolation over seamless sync.
If you forget your master password, your data is gone forever. We cannot help you recover it. If that scares you, please stick to cloud managers.
Passary adds friction by design. You manage the file. You manage the backups. If you want "set and forget", this is not the tool for you.
Passary uses industry-standard cryptography you'd expect — not proprietary obscure algorithms. Below is a clear rundown of the technical guarantees you should expect:
Argon2id with bounded time cryptographic hash using a large salt and key derivation function. High cost makes brute-force attacks impractical.
Vault content encrypted with AES-256-GCM to provide confidentiality and integrity — encryption fails if even one bit is tampered with.
When you open a vault, keys only exist in memory and are never cached, making it relatively clean (nothing in cleartext stored in directories, no sneaky caching on refresh or close).
Passary never sees your master password or decrypted vault. Without the key yourself, the vault is and will remain mathematically irrecoverable.
If this doesn't hit your spec, including latest PII parameters and encryption modes, see the detailed security model page.
Read the full security model →Stop using "Password123". Passary's built-in generator creates cryptographically secure passwords that are mathematically impossible to guess.
The era of "just put it in the cloud" is ending. With increasing data breaches, vendor lock-in, and privacy erosion, the future belongs to Local-First Software.
Passary is more than a tool; it's a philosophy. Your data should be yours. It should live on your device, under your control, encrypted by keys only you hold.
Passary is designed to know nothing about you. We have no accounts, no analytics tracking, no telemetry, and no access to your data.
Yes. Passary runs legally in your browser but never sends your vault data to any server. Once the app loads, you can even disconnect your internet. Your vault file is stored in your browser's local storage or saved to your file system.
If you lose your vault file (and have no backups), your data is lost. Passary does not have a copy. We strongly recommend keeping backups on a USB drive or your personal cloud storage.
Not automatically. To use Passary on another device, you must manually transfer your vault file (e.g., via USB, Airdrop, or a synced folder like Dropbox/iCloud).
Passary is inspired by KeePass but built for the modern web. It requires no installation, runs on any device with a browser, and uses a modern, user-friendly interface.
Yes. Passary uses the Web Crypto API, which provides native, high-performance cryptographic primitives (AES-GCM, Argon2id) isolated within the browser context. We also use strict Content Security Policies.